Every now and then, a new technology phrase emerges. It’s all around you, but you’re not sure what it is. Cloud computing became the buzzword on everyone’s lips a few years ago. Edge Computing appeared just as you were starting to grasp what it was all about. We are here to help you in understanding edge computing. So, here’s the question:
What is Edge Computing?
Edge computing occurs when activities are carried out at the logical location nearest to the user. Locally on a device is frequently the most logical and efficient location for data processing. It may be at the nearest data center at times. In essence, Edge Computing is data processing that takes place off the network, at the network’s ‘edge,’ and closer to the source of the data. If the data is sent to the cloud at all, it is only after it has been analyzed and polished. With the growing popularity of the Internet of Things (IoT), edge computing is becoming increasingly important.
Edge Computing In The Internet Of Things?
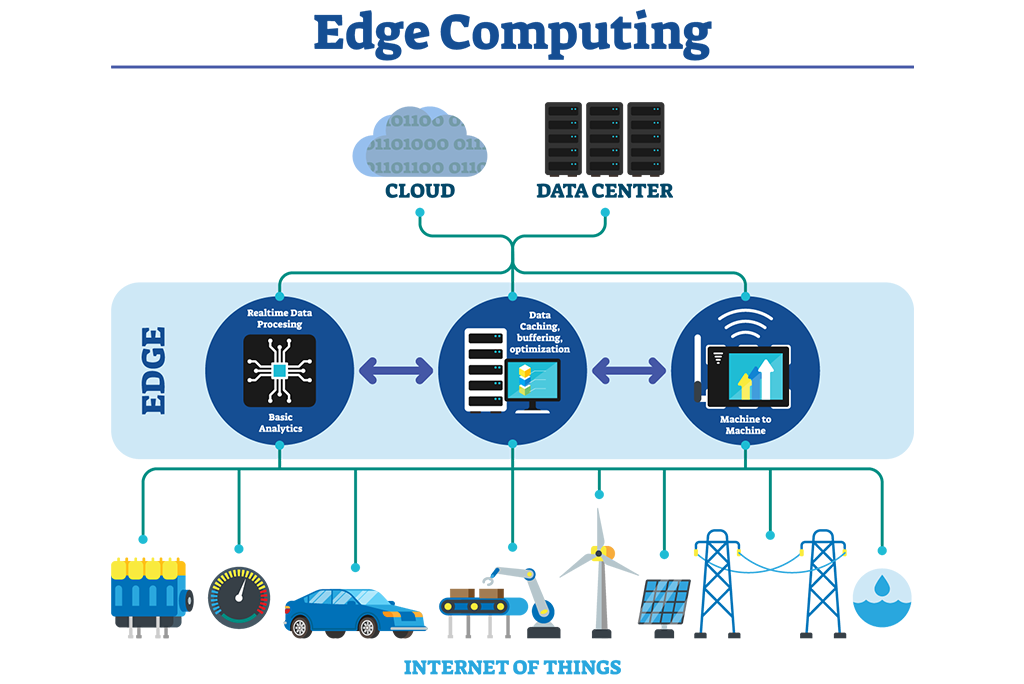
Photo Credit: innovationatwork.ieee.org
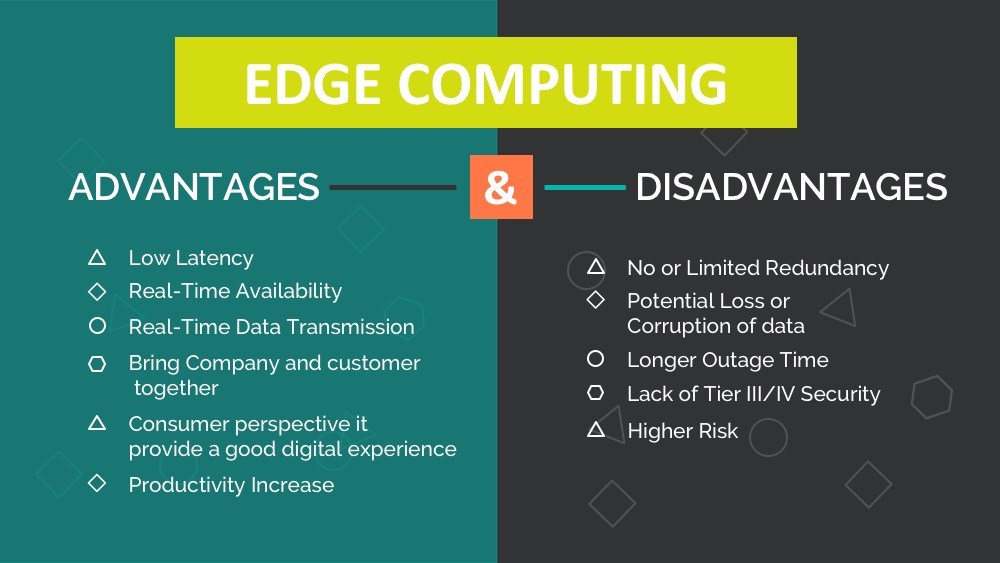
Reducing Latency
Latency is the time it takes for you to make a query to the network through your device and for a response to arrive. Smart devices connected to the Internet operate at a fraction of the speed of human intellect. Factors such as bandwidth, network speed, and even distance from the server or database limit them. We may be oblivious to the time lag or latency most of the time, but it exists. Most of the time, this will have no effect on the device’s performance. However, in other circumstances, the latency could be detrimental. A self-driving car, for example, cannot afford to lose its ability to make split-second choices while on the road because the network is congested. Edge Computing enables such devices to compute and make decisions at a rapid rate on the fly, without sacrificing efficiency.
Enhancing Security
Even the most protected databases, as recent news has shown, are not completely safe. Any data kept in the cloud can be hacked, exposing the personal information of your users. While the device collects a lot of data, only the necessary data is transferred to the cloud with Edge Computing. In some circumstances, the device isn’t even always connected to the internet. This means that even if the cloud is hacked, not all of the user’s information is at risk. Because there are less data going to the cloud, the data cannot be intercepted while being sent. That isn’t to suggest Edge Computing is without security flaws. This technology, on the other hand, reduces the quantity of data that may be at risk in the cloud.
Reducing Infrastructure Needs
While your users may not realize it, cloud computing necessitates a vast infrastructure to support it. Edge Computing allows you to reduce the amount of infrastructure required. Rather than having to enlarge servers to accommodate all of the data, the data is saved on the user’s device. This also makes it easier for your business to grow without having to invest in new infrastructure. It also implies that your customers will be able to use the service at no additional expense.
Improving Reliability
Distributed Denial of Service (DDoS) attacks can affect cloud-based services. A DDoS attack occurs when a server is inundated with fake inquiries, clogging the network and preventing legitimate users from accessing it. With Edge Computing, you can avoid this and provide your consumers with uninterrupted service. Edge Computing also eliminates the risk of network failures or sluggish connections because it does not rely on a constant connection to the Internet or servers. One of the most significant advantages of Edge Computing is this. It can be utilized for operations in remote regions or areas where a stable network connection is unavailable.
How Are IoT And Edge Related?
The Internet of Things benefits from having processing power closer to the physical device or data source. The data created by IoT sensors and devices must be examined at the edge, rather than traveling back to a central site, in order for it to be used to react faster or reduce issues.
Edge computing minimizes the latency of communication between IoT devices and the central IT networks to which they are connected by providing a local source of processing and storage for the data and computing demands of IoT devices.
Without edge computing, IoT would rely on cloud or datacenter connectivity and compute services. Sending data back and forth between an IoT device and the cloud might cause response times to be slower and operational efficiency to be poorer.
Other difficulties addressed by edge computing include the network bandwidth required to transfer huge volumes of data across slow cellular or satellite connections, as well as the ability for systems to work offline if a network connection is lost.
You may use edge computing to take advantage of the massive amounts of data generated by connected IoT devices. By deploying analytics algorithms and machine learning models to the edge, data may be processed locally and used to make quick decisions. Data can also be aggregated at the edge before being transferred to a centralized location for processing or long-term storage.
What Are Some Real-Life Uses Of Edge Computing?
Edge Computing’s speed and durability make it perfect for usage in a variety of industries, including:
-
Self-Driving Vehicles
-
Fleet Management
-
Traffic Management
-
Power Management With Smart Grids & Smart Meters
-
Safety Monitoring In Remote Oil And Gas Rigs
-
Smart Video Orchestration
-
Mobile App Data Management
-
Stock Market Trading
-
Gaming
Edge Computing, on the other hand, is not without its downsides. It still has a few drawbacks as an emerging technology.
What Are The Disadvantages?
Edge Computing has both a disadvantage and an advantage in terms of security, as bizarre as that may sound. One danger of IoT devices is that they can be hacked by the data they collect. It is possible to deceive the gadget about the data it has collected if it is hacked, resulting in ‘bad decisions. The security of IoT devices becomes more critical as a result of this technology. If it isn’t up to par, all of the device’s data could be compromised. Hackers may be able to gain access to the core network as a result.
Smart devices that use Edge Computing must be protected both physically and in terms of the data, they carry. They can be tampered with if they aren’t. When connected to the network, IoT devices should, whenever possible, be connected via wires. Instead of being open, the WiFi network should be shut down. The gadgets should be designed in such a way that the user can change the default login to something more secure. In addition, data encryption, firewalls, and intrusion detection and prevention systems should be in place.
Furthermore, as the Internet of Things (IoT) grows in popularity, a growing number of gadgets are becoming “smart.” Regrettably, there is currently no standardized security policy in place for all of them. This means that it is up to the developers to determine how secure your IoT gadget is. Of course, as this technology advances, the scenario may alter. As things stand, this is still the most significant disadvantage of Edge Computing.
Localized information is fantastic for users. However, as the service provider, you risk losing a significant amount of user activity data. Because the local device determines which data is sent to the main information center, you may not get a complete picture of your business operations and how your customers utilize your service.
Your consumers may require extra storage on their device as a result of Edge Computing, which may affect the device’s size. Given how powerful and compact computing and storage technologies are developing, this may not be a significant usability issue. However, it is something to think about while creating an IoT gadget. In essence, Edge Computing enables you to provide fast and dependable service to your consumers that are not constrained by network or bandwidth limitations.
Protecting The Edge With AKCP
AKCP monitoring solutions allow you to gain detailed insights into your data center facility’s environmental and power parameters. Checking for hotspots, differential air pressure, and airflow around your data center. Ensure that real-life measurements match predicted cooling and airflow analysis from CFD models. Once you have the proper sensors and monitoring in place, the measurements can be used to begin controlling your data center for maximum efficiency. The first thing to do is determine what is your current PUE and use this as a benchmark.
The PUE computations on the AKCPro Server are updated in real-time. The overall facility and IT loads are used as the input using power meters. The PUE that results is dynamically presented. The live PUE values will update as your facility loads vary. Make modifications to your facilities and see how much energy you save right now. You can achieve maximum PUE while staying within ASHRAE suggested inlet air temperatures by using cabinet thermal maps. Cabinet thermal maps also keep track of the T across the rack to guarantee proper cooling.
Try out our online PUE Calculation Tool here
AKCPro Server produces a graph of your PUE by continuously monitoring it over time. This enables data center managers to assess the impact of modifications on PUE and track progress. You can ensure optimal data center efficiency by combining PUE metrics with other sensor data. You may have a fantastic PUE of 1.25, but half of your servers are idle. When they spool up, what happens? Is the cooling capability being used to its maximum potential? Are you running your data center at an uncomfortably low temperature?
Reference Link:
https://www.dcsl.com/everything-you-need-to-know-about-edge-computing/
https://www.machinemetrics.com/blog/edge-computing-iot
https://searchdatacenter.techtarget.com/definition/edge-computing
https://www.microsoft.com/en-us/edge/features